The Directive on Security of Network and Information Systems (EU) 2022/2555, commonly known as NIS2, is a comprehensive piece of European Union legislation aimed at enhancing cybersecurity across Europe. Since its entry into force on January 16, 2023, EU Member States have 21 months to incorporate its provisions into their national laws.
Overview of NIS2
If your company provides services to the European economy and society, this directive likely applies to you. In a previous article on NIS2, we discussed in detail which organizations are affected by the directive: How to Check if NIS2 Applies to Your Organization? | C&C Partners (ccpartners.pl).
It is essential to understand how the NIS2 directive may impact your current cybersecurity posture. To avoid severe penalties for non-compliance, you must develop a clear compliance approach and strategy. This is not only about avoiding financial fines; NIS2 mandates stronger oversight, enforcement, and personal accountability for management teams.
In our article, you will find detailed information about NIS2, including which organizations fall within its scope, specific details for various industry sectors, and what actions your company must take to comply. We also explore the financial penalties and other liabilities your business could face if NIS2 compliance is not taken seriously.
Why do we need NIS2?
The original NIS regulations were introduced in response to growing concerns about cybersecurity and the evolving threat landscape. However, events in recent years—such as the COVID-19 pandemic, Russia's invasion of Ukraine, and the continuous rise in various types of cyberattacks—prompted the EU to expand and strengthen the initial directive, resulting in NIS2.
The impact of this new directive could be as significant as GDPR, making it crucial to be aware of the upcoming requirements. NIS2 aims to address the shortcomings of its predecessor through national cybersecurity strategies, enhanced cooperation and information sharing among member states, increased responsibilities for risk management and incident reporting, as well as stricter regulatory oversight and enforcement.
While GDPR focuses on personal data protection and privacy rights, NIS2 emphasizes the security and resilience of networks and information systems, particularly in organizations critical to the functioning of modern society.
Categories of entities in NIS1 (2016) and NIS2
The 2016 directive identified two types of organizations:
- Essential services – including providers in sectors such as energy, transport, water, and healthcare.
- Digital service providers – such as online marketplaces, cloud services, and search engines.
Organizations falling into one of these categories were required to meet three main obligations:
- Implement appropriate security measures to protect against cyber threats.
- Report incidents that significantly impacted their operations.
- Notify the relevant authorities about major incidents.
Under the original legislation, EU member states had the authority to determine the types of businesses required to comply with NIS. However, NIS2 introduces updated terminology, referring to "essential entities" and "important entities," while also providing more precise definitions of the types of businesses within these categories.
The NIS2 directive applies not only to organizations based within the EU but also to those outside the EU that offer services within its territory. Member states are now obligated to maintain an up-to-date list of all essential and important entities operating under their jurisdiction.
Penalties and sanctions for NIS2 non-compliance
While NIS2 brings significant benefits, it also poses challenges related to implementation and compliance. For some organizations, particularly smaller ones, this can be difficult as they face additional costs and resource requirements.
The directive outlines both monetary penalties and non-financial sanctions, as well as the potential for criminal penalties in certain circumstances.
Non-financial measures
As part of the enforcement framework, NIS2 empowers national supervisory authorities to impose non-financial sanctions, including:
- Binding instructions – requiring organizations to take specific actions to address vulnerabilities or improve security measures.
- Mandatory security audits – compelling entities to undergo external or internal reviews of their cybersecurity practices.
- Customer notifications – obliging organizations to inform customers about potential threats or breaches that may affect them.
- Compliance orders – enforcing adherence to the requirements set out in the directive.
These measures aim to ensure that organizations not only rectify immediate issues but also establish stronger security practices to prevent future incidents.
If your company is subject to the NIS2 directive, it’s essential to consider the broader non-financial consequences of a serious cybersecurity breach and its cascading effects. Depending on the nature of the attack and the lack or inadequacy of security measures that enabled the breach, trust from customers, partners, and investors could erode significantly.
- Customer Trust: Clients may hesitate to purchase products or services, fearing further vulnerabilities.
- Partnership Stability: Business partners might seek more reliable providers to minimize their exposure to risk.
- Investor Confidence: Investors could withdraw support, seeing the company as a high-risk venture.
Reputational damage
The reputational harm resulting from a breach is challenging to quantify but should be a critical factor in risk management planning. Organizations might also face difficulty collaborating with others, as partners may prioritize working with businesses compliant with NIS2 to safeguard their own operations.
Moreover, failure to take compliance seriously could lead to competitive disadvantages. Companies adhering to NIS2 will likely gain a reputation for reliability and security, setting higher standards in the industry.
Talent attraction and retention
A poor reputation in cybersecurity can deter top IT and cybersecurity professionals from joining your organization. Skilled talent often prefers employers known for robust security practices and proactive approaches to compliance and risk management.
By prioritizing compliance and demonstrating a commitment to cybersecurity excellence, your company can mitigate these risks and maintain trust across all stakeholders.
Administrative penalties
Under the NIS2 directive, administrative penalties are distinctly categorized based on the entity's classification as either essential or important.
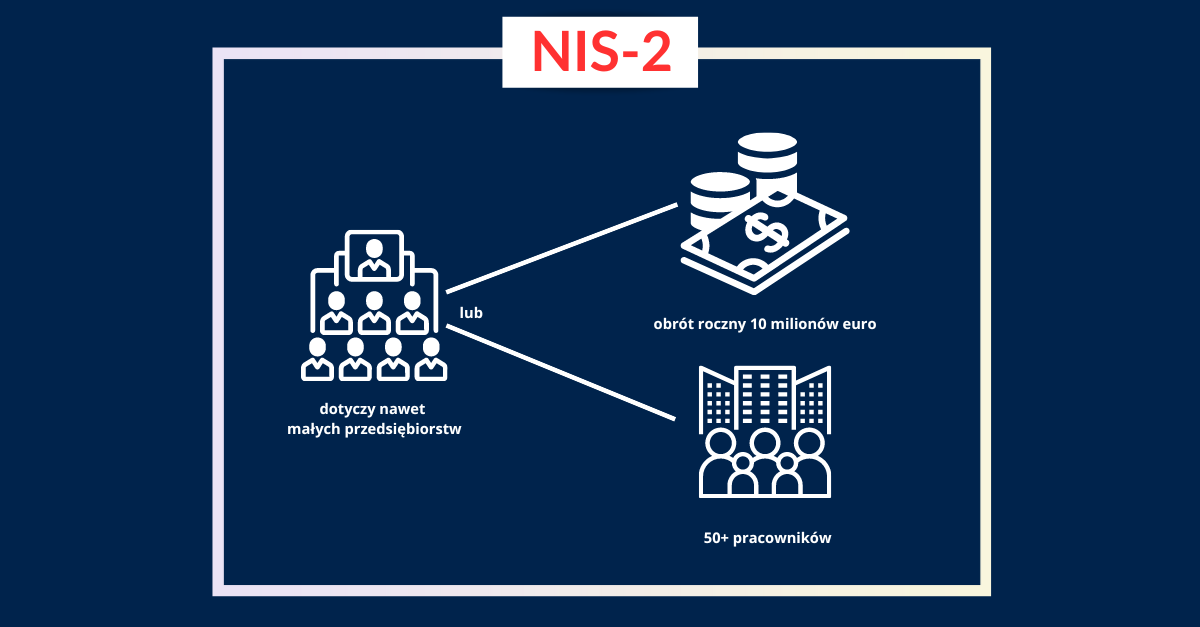
- Essential Entities: Member states must establish maximum fines of at least €10 million or 2% of global annual revenue, whichever is higher.
- Important Entities: For these entities, member states are mandated to impose fines up to a maximum of €7 million or 1.4% of global annual revenue, choosing the higher value.
This differentiation highlights a tiered approach to penalties based on an organization's classification. Importantly, many "important entities" are subject to such regulations for the first time under NIS2. Compliance for smaller organizations, in particular, may appear daunting due to the additional demands on resources and effort.
Both SMEs and larger companies will need to invest significant resources to ensure their cybersecurity practices are robust enough to meet NIS2 audit requirements. These adjustments require dedicated time, focus, and financial investment. For SMEs especially, the cost of improving cybersecurity to comply with the directive must be factored into budgets, as meeting the required defense standards may necessitate extensive process and system upgrades.
Criminal sanctions for management
To reduce the burden on IT departments, traditionally seen as solely responsible for organizational security, and to shift accountability to leadership, NIS2 introduces measures that impose personal liability on senior management for gross negligence in cybersecurity breaches.
The directive explicitly empowers enforcement authorities to hold board members personally accountable in cases of severe oversight failures following a cyber disaster. These powers include:
- Public Breach Notifications: Organizations must report non-compliance breaches publicly.
- Individual Identification: Authorities can publish statements naming individuals and organizations responsible for the breach, along with the nature of the misconduct.
- Temporary Bans on Leadership Roles: For essential entities, repeat violations can result in a temporary prohibition on holding managerial positions.
This shift aims to elevate cybersecurity to a board-level priority, emphasizing that lapses in compliance have both organizational and personal consequences. By doing so, NIS2 seeks to foster a culture of shared responsibility for cybersecurity across all levels of an organization.
Incident reporting under NIS2
In the event of a breach or incident, organizations must follow a three-step reporting procedure:
- Initial alert: A preliminary warning must be submitted to the relevant authority within 24 hours of detecting the incident.
- Formal notification: A more detailed incident notification must follow within 72 hours.
- Final report: The organization must deliver a comprehensive final report within one month of the formal notification. Organizations are also required to respond to status update requests and provide progress reports as needed.
Incidents under NIS2 may also qualify as breaches under the GDPR. If this occurs, NIS2 will not impose a financial penalty for the same incident. However, non-financial sanctions under NIS2 may still apply.
Next steps toward NIS2 compliance
While no immediate actions are required until NIS2 is fully implemented in your organization, many of the measures outlined in the directive align with best practices for safeguarding critical business data.
These include:
- Conducting a Data Audit: Identify the cloud services and SaaS applications used to store and process your company’s data.
- Regular Cybersecurity Reviews: Assess existing tools and strategies to ensure compliance and preparedness before a breach occurs.
- Data Encryption: Encrypt data both in transit and at rest.
- Reliable Backup Solutions: Maintain robust backup solutions for all data, including those stored in SaaS applications.
- Disaster Recovery Strategy: Develop and regularly test a comprehensive data recovery and business continuity plan to address breaches, particularly involving corporate emails.
- Cybersecurity Training: Provide regular cybersecurity training sessions for all employees and schedule periodic refresher courses.
Cybersecurity: a continuous effort
Cybersecurity is not a one-time task; it is an ongoing challenge. As cyber threats evolve, organizations must continually adapt their defenses. Emerging attack techniques, vulnerabilities, and malicious actors necessitate a proactive and dynamic approach to security.
The NIS2 directive sets a new standard that every modern organization should embrace to operate safely in today’s hyper-connected environment. Adhering to NIS2 is not just about avoiding penalties—it is about securing your company’s future in an era of digital conflict.

 Share on
Share on
 Share on
Share on
 Share on
Share on
